Data Security, Powered by Coro
Comprehensive Cybersecurity, Simplified
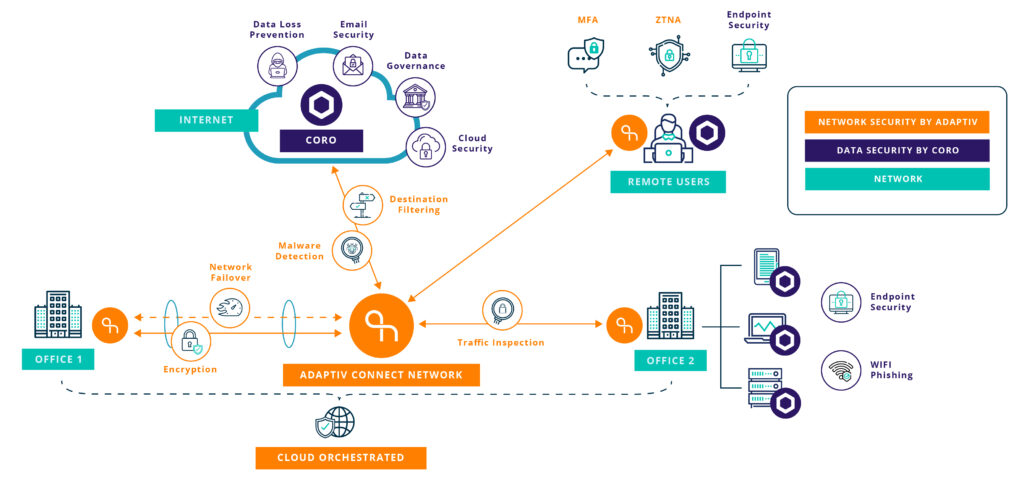
Coro data security and endpoint protection solutions fit perfectly with Adaptiv Networks’ multi-layered network security, offering you added peace of mind that comes with a comprehensive cybersecurity strategy.

Why Coro?
Adaptiv SD-WAN and SASE solutions protect against threats moving through your network, but what about threats that are lurking in data that’s stored in your cloud servers, emails or employee devices?
Coro adds protection for data and endpoints that complements Adaptiv’s network security to create a comprehensive cybersecurity posture. With no complicated integrations, and no technical challenges, Coro solutions are ideal for SMEs with lean IT teams. Simply choose a Coro cybersecurity suite that fits your business, or Coro AI Complete for total protection.
How Coro Simplifies Data Security and Endpoint Protection
Building a cybersecurity stack has always meant buying multiple, segmented tools from multiple vendors, training employees on each one, and dealing with multiple interfaces and endpoint agents. Until now. Coro is one platform with many modules. Get all the security you need now, with the ability to switch on any module you need in the future.
One Interface
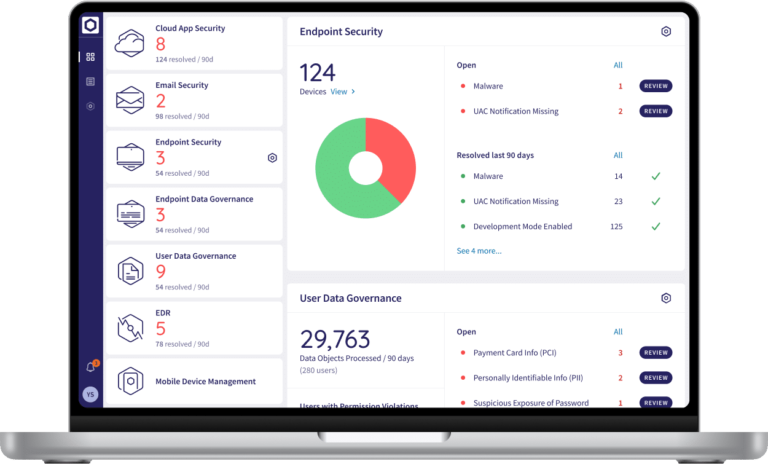
All modules feed into one, easy-to-use dashboard, in which you can quickly view and even respond to statuses, events, and logs.
One Endpoint Agent
Device posture, NGAV, EDR, VPN, firewall, and data governance on one easy-to-manage endpoint agent, eliminating agent conflicts.
One Data Engine
Modules inform each other through a shared data engine, eliminating the need for integration and improving security posture.
Coro cybersecurity suites tailored to fit your business needs
 Get Coro’s full range of security modules for comprehensive coverage and automatic incident resolution.
Get Coro’s full range of security modules for comprehensive coverage and automatic incident resolution.
Included Modules:
- Endpoint Security
- Endpoint Detection & Response (EDR)
- Email Security
- Cloud App Security
- Network
- Endpoint Data Governance
- User Data Governance
- Mobile Device Management
- Security Awareness Training
- Inbound Gateway
- Secure Messages
- Secure Web Gateway
- Wifi Phishing
 Get essential coverage for endpoints, email, and cloud apps, automating resolution of most security incidents.
Get essential coverage for endpoints, email, and cloud apps, automating resolution of most security incidents.
Included Modules:
- Endpoint Security
- Endpoint Detection & Response (EDR)
- Email Security
- Cloud App Security
- Secure Messages
- Inbound Gateway
- Wifi Phishing
 Log all endpoint activity, analyze data anomalies, and automate resolution of most security incidents.
Log all endpoint activity, analyze data anomalies, and automate resolution of most security incidents.
Included Modules:
- Endpoint Security
- Endpoint Detection & Response (EDR)
- Endpoint Data Governance
- Wifi Phishing
Explore Coro Cybersecurity Modules
Coro modules are self-contained security components that can be turned on or off within the Coro platform. Each module performs as well as, or better than, legacy solutions in its security domain. Our Coro suites bundle multiple modules together into affordable cybersecurity solutions.
Safeguard endpoint devices and protect your business with the Coro Endpoint Security module. It automatically identifies and logs all devices, scanning for malware, suspicious activity, and human errors. The Endpoint Security module detects unusual behavior and neutralizes threats before they can cause harm.
Capabilities:
- Device Posture: Sets device policies according to device vulnerabilities
- Allow/Block Lists: Creates allowlists and blocklists for files, folders, and processes to reduce tickets triggered by unknown activities
- Advanced Threat Control: Blocks any processes that exhibit suspicious behavior
- Scheduled Malware Scans: Schedules daily, weekly, or off-hours malware scans on Windows, macOS, and Linux agents
- Multilingual Support: Provides additional support for Spanish, Italian and French
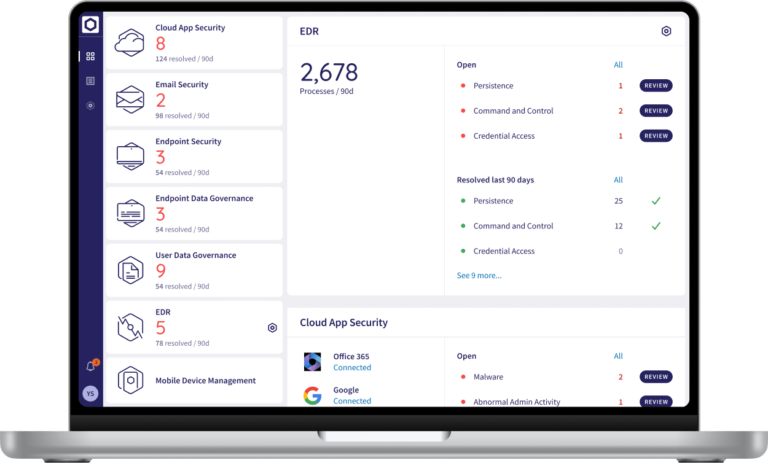
Coro’s Endpoint Detection & Response (EDR) module provides proactive, real-time protection for interconnected endpoint devices and the broader network against sophisticated cyber threats. Leveraging behavior-based detection and continuous monitoring, Coro EDR identifies threats in real-time, preventing them from going unnoticed for extended periods.
Capabilities:
- Telemetry Tab: Collects and organizes forensic details from devices
- Process Graph: Visualizes process lineage and parent-child relationships to trace threats
- Process Tab: Displays an aggregated view of all executed processes
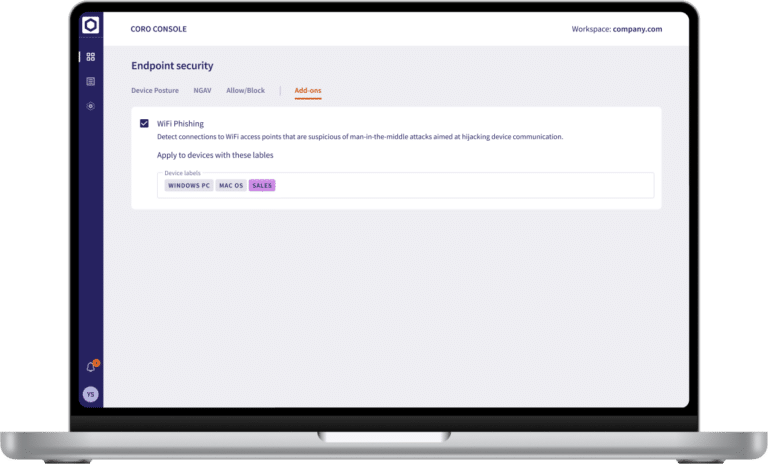
The Coro WiFi Phishing add-on guards endpoints outside the LAN (local area network) by preventing connections to suspicious WiFi access points. It works by detecting connections to WiFi access points that are suspicious of man-in-the-middle attacks aimed at hijacking device communication.
Protects:
- All devices in your workspace
- Specific groups of devices
- Remote / traveling employees
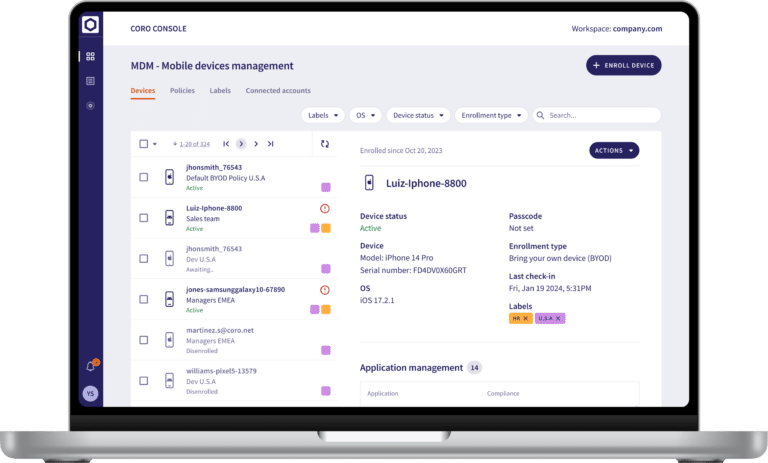
Coro’s Mobile Device Management (MDM) module simplifies the management and security of company-owned and Bring Your Own Device (BYOD) work-related mobile devices. It enables IT teams to enforce app policies, manage apps, and ensure company policy compliance. The module gives visibility into mobile devices, ensuring efficient device management across the organization.
Capabilities:
- iOS and iPadOS Device Enrollment: Enrolls devices via DEP or through MAID
- Application Policy: Defines and enforces rules for app use, including install/remove restrictions, blocking in-app purchases, and locking system defaults
- Lost Mode: Locks supervised devices, shows custom contact info, and tracks location when powered on
- Remote App Installation: Installs required apps on employee devices directly from the console
- Device Management: Remotely wipes data from compromised devices, marks devices for disenrollment to remove profiles and policies, and removes devices that are inactive or disenrolled
- Multilingual Support: Provides additional support for Spanish, Italian and French

Experience advanced email protection that safeguards your business against data leaks and social engineering attacks with ease. Powered by Coro’s intelligent engine and Large Language Models (LLMs), the Coro Email Security module automatically monitors, detects, flags, prioritizes, quarantines, and remediates the most advanced threats. Leveraging advanced LLMs increases phishing attack detection accuracy and strengthens the system’s capabilities.
Capabilities:
- Outbound Gateway: Enables real-time monitoring and blocking of outbound emails that violate an organization’s sensitive data policies
- API-Based Cloud Email Protection: Integrates directly with API-based email providers with no installation or hardware required
- Quarantine / Warn Modes: Isolates suspicious emails or flags them with alerts for review
- Allow / Block Lists: Defines trusted senders or blocks specific domains to control access
- Multilingual Support: Provides additional support for Spanish, Italian and French

Coro Secure Messages add-on lets you encrypt outbound emails. With this module, you can use a private key to ensure only the intended recipients can access emails.
Works with:
- Microsoft O365
- Google Workspaces
- Desktop email
- Mobile email apps

The Coro Inbound Gateway add-on is a proxy that provides real-time detection and protection for incoming emails. It lets you intercept inbound emails and inspect them, allowing only threat-free or trusted emails to reach recipients.
You can choose between the following for suspicious emails:
- Warning Only: Emails are not blocked but are marked with explanatory warnings for the recipients
- Block: Emails are blocked and can only be released from quarantine by workspace administrators

Coro’s Cloud App Security module provides advanced malware detection and robust remediation capabilities to protect users, their cloud drives and apps. By securely connecting cloud applications, Coro ensures monitored, protected, and controlled user access, enabling businesses to safeguard data and apps against a wide variety of threats.
Capabilities:
- Cloud Applications: Connects, monitors and controls a range of cloud apps: Microsoft Office 365, Google Workspace, Slack, Dropbox, Box, and Salesforce
- Access Permissions: Allows admins to set permissions for specific groups, specific users, or all users, with access restricted by country or IP
- Impossible Traveler: Detects login attempts from distant locations in unrealistically short intervals, helping identify potential credential compromise or unauthorized access
- Dedicated “Quarantine” Folder: Stores detected malicious files in the “Suspected folder” and creates a ticket for the event
- Third Party Applications Tab: Lists and manages third-party apps connected to MS 365 and Google Workspace, offering control and visibility into app usage within the organization
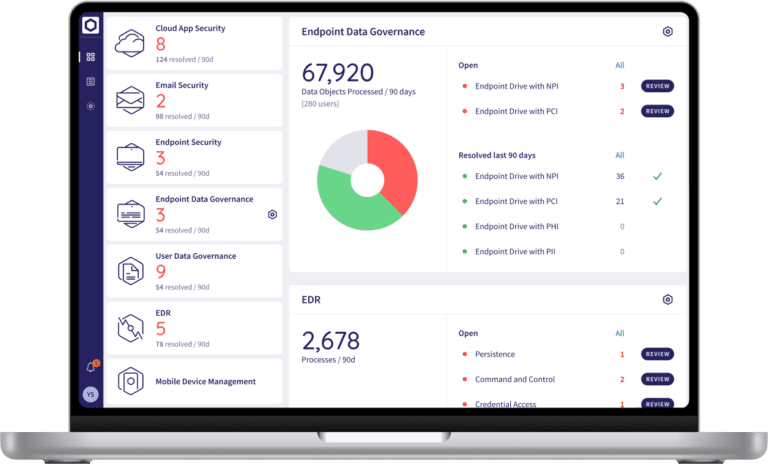
Coro’s Endpoint Data Governance module protects sensitive and critical data on endpoint devices. It monitors how data on these devices is stored, detecting and preventing unauthorized use, accidental loss, risky data sharing, or violations of data protection policies. Endpoint Data Governance comes pre-configured with baseline security policies and ensures endpoint devices comply with data protection policies from day one.
Capabilities:
- Regulatory Data Configuration: Enables the configuration of various sensitive data types, such as PHI, PCI, PII, and NPI, ensuring compliance with data protection laws
- Manual Scanning: Provides the ability to perform on-demand scans from the Coro Console of endpoint devices to check for sensitive data exposure (e.g., PHI, PCI, PII, NPI) and mitigate risks in real-time
- Scheduled Scans: Admins can schedule automated scans on endpoint devices to check for sensitive data stored on storage drives, ensuring continuous protection and early detection of potential risks
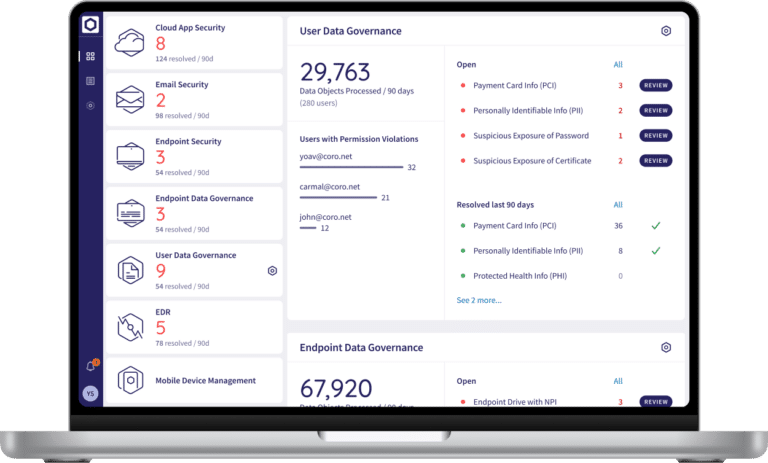
The Coro User Data Governance module enables businesses to detect unauthorized sharing or access of sensitive data. Through continuous monitoring of user behavior and data exposure, it ensures that sensitive data such as personal details, health records, and payment information is only accessible to authorized individuals and compliant with data protection regulations such as GDPR, HIPAA, and PCI-DSS.
Capabilities:
- Outbound Gateway: Enables real-time monitoring and blocking of outbound emails that violate an organization’s sensitive data policies
- Regulatory Data Configuration: Enables the configuration of various sensitive data types, such as PHI, PCI, PII, and NPI, ensuring compliance with data protection laws
- Continuous Monitoring: Monitors and scans unusual data-sharing activities that might expose sensitive data (PHI, PCI, PII, NPI) via email or file-sharing
- Access Permissions: Allows administrators to control user access to sensitive data by setting specific permissions for individuals, groups, or domains
- Exclusions: Allows administrators to exclude emails from sensitive data scans based on specified keywords in the subject line
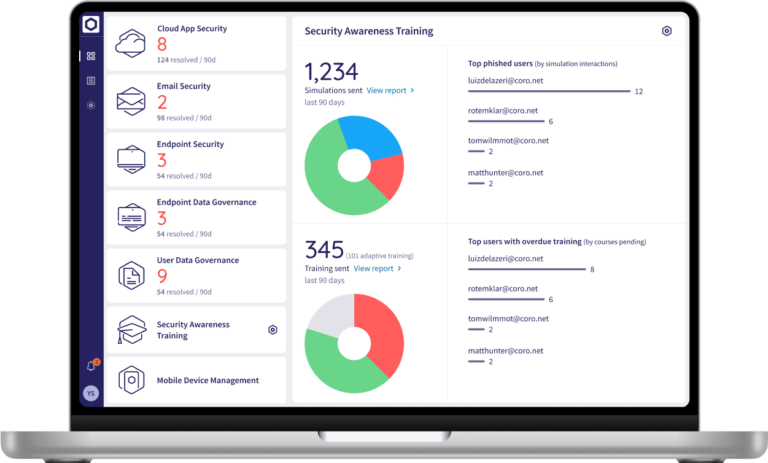
Coro’s Security Awareness Training (SAT) module empowers leadership, employees and contractors with the knowledge and tools to recognize phishing and social engineering attacks. SAT reduces human error and strengthens your cybersecurity posture through real-world phishing simulations and high-quality security awareness training. Using SAT shows that your business has proactively implemented security awareness measures, mitigating legal, financial, insurance, and reputational risks while safeguarding your organization and leadership.
Capabilities:
- Phishing Simulations: Simulates phishing attacks to assess vulnerabilities and raise awareness
- Adaptive Training: Uses adaptive training to personalize learning based on security risks and user behavior
- Training Courses: Delivers focused courses on best-practice cybersecurity via videos and quizzes
- Reporting: Delivers powerful analytics including simulations engagement, phishing failure and training completion rates
Adaptiv SD-WAN
Business Connect
Business Connect
Enterprise Connect
Enterprise Connect
My Connect
Adaptiv SASE
Network Security by Adaptiv
Data Security by CORO
Web Connect
Network Connect
Coro AI Complete
Coro AI Essentials
Coro AI Endpoint
Bandwidth-based license
User/Device-based license
Comprehensive Network and Data Security
Adaptiv SD-WAN provides network security that fits perfectly with Coro data and enpoint security to provide comprehesive protection.
Frequently asked questions
Coro by Adaptiv Networks
No. Coro is a software-based soluton, a client applications is installed on user endpoints with no hardware required.
Yes. Coro can be integrated with existing cybersecurity solutions so you can choose whichever modules you need to address security gaps. Over time you can use additional Coro modules to bring all your cybersecurity into a single platform.
Yes, we do offer the option to puchase individual Coro modules. The suites offer compelling value because they are simple and you get more for your money, however we can also provide quotes for individual Coro modules on request.
Yes! Coro solutions work perfectly with ELFIQ link balancing and SD-WAN solutions. Al the Coro suites and modules are available for ELFIQ customers



